Do you have a jar full of coins collecting dust on a shelf or hidden in a kitchen drawer? You’re certainly not alone—millions of people treat loose change as a casual savings account, but few realize the potential value locked inside. Before you drag that heavy jar to the nearest bank or pour it into a coin-counting machine, understanding the real worth of your stash and grading coins in it is crucial. Here’s why:
- Avoid Surprises: Without an accurate estimate, you might be shocked at how much—or how little—your change is worth when you finally cash it in.
- Spot Hidden Gems: Some coins have significant numismatic (collector) value. Recognizing rare pieces early can prevent you from accidentally giving away something worth hundreds of dollars.
- Save Time and Effort: Knowing the approximate total value can help you decide whether it’s worth visiting a coin dealer, rolling your coins for the bank, or using a coin-counting service.
The true cost of ignoring your change jar isn’t just about missed dollars—it’s about lost opportunities. A few pennies could be an overlooked treasure.
Traditional Methods: Weighing and Guessing
Before the age of AI-driven apps and online databases, people relied on physical methods to estimate the value of loose change. Although these techniques may seem old-fashioned, they still offer a surprisingly reliable ballpark figure—especially if you’re looking for a quick assessment without the hassle of counting individual coins.
Step-by-Step: How to Estimate Using Weight
Here’s a basic, effective approach:
- Sort by Denomination: Separate your coins into four groups: pennies, nickels, dimes, and quarters.
- Weigh Each Pile: Use a precise kitchen scale, ideally one that measures in grams.
- Calculate Totals: Based on standard coin weights, apply the following:
| Coin Type | Weight per Coin | Face Value |
| Quarter (since 1965) | 5.670 grams | $0.25 |
| Dime (since 1965) | 2.268 grams | $0.10 |
| Nickel | 5.000 grams | $0.05 |
| Penny (post-1982) | 2.805 grams | $0.01 |
- Do the Math:
- Divide the total weight of each pile by the weight of a single coin to find the number of coins.
- Multiply the number of coins by the coin’s face value to get the total value for that denomination.
- Add all denominations together for an estimated total.
For Mixed Jars: Quick Estimation Using Averages
If your change jar is too messy to sort easily, online calculators like the one at vCalc can help. These calculators use statistical averages based on real-world research. For example, a typical jar might have:
| Coin Type | Average Distribution (%) |
| Quarters | 31.9% |
| Dimes | 17.0% |
| Nickels | 8.5% |
| Pennies | 42.6% |
Using this method:
- Multiply the total weight by the probability of each coin type.
- Divide by the individual coin weight to estimate the number of each coin.
- Multiply by face value to estimate the total worth.
The vCalc Guide simplifies it:
“Multiply the coin weight by each coin probability. This results in the total weights of each coin type in the container. Divide each total coin weight by the weight of the individual coin to get the count, then multiply by the coin’s value.”
This technique can yield a surprisingly accurate estimate with minimal effort—perfect for busy people who still want to get a reasonable idea before heading to the bank.
Modern Solutions: Coin Scanning Apps
One of the most powerful tools available today is the Coin ID Scanner app. By leveraging the power of your smartphone’s camera and cutting-edge AI technology, this app transforms the tedious process of coin estimation into a few simple taps.
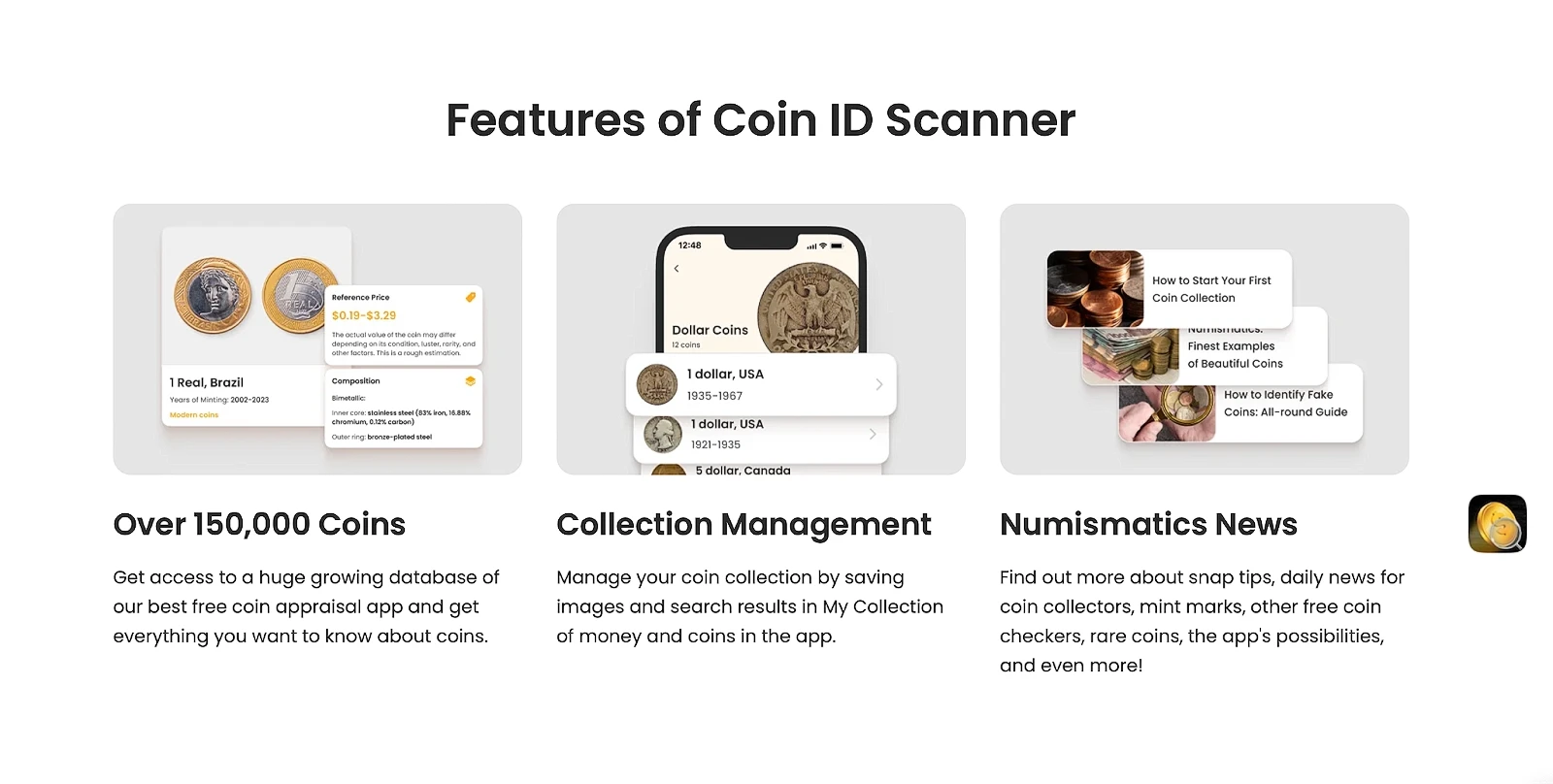
Key Features of Coin ID Scanner
- Instant Identification: Recognizes coin denominations, years, and even subtle mint marks within seconds.
- Value Estimation: Provides current market value for common, rare, and collectible coins based on reputable numismatic databases.
- Catalog Management: Allows users to organize coins into collections, making it easy to track valuable finds and duplicate items.
- High Accuracy: Continuously updated algorithms ensure precise recognition and valuation, minimizing human error.
Why It Matters:
If you’ve ever wondered whether that tarnished old dime might be a valuable 1970-S proof or a 1942 silver dime, the Coin ID Scanner app eliminates guesswork. It flags coins that could have higher value, helping you separate ordinary change from potential treasures.
How to Use Coin ID Scanner Effectively
- Spread your coins on a clean, well-lit surface.
- Open the app and activate the scanning feature.
- Slowly move your camera over the coins; the app will highlight, identify, and estimate values in real-time.
- Review flagged coins separately for more detailed inspection.
By streamlining what used to be hours of sorting and research into mere minutes, Coin ID Scanner empowers everyday savers and budding collectors alike.
Top Online Resources for Coin Values
If you want to dig deeper into coin values or research specific coins, these reputable sites are essential:
| Website | Features |
| Coin ID Scanner | A website with vast coin catalogue and professional blog; convenient app with AI-based instant coin identifier and instruments for collection organization. |
| CoinValueChecker | Comprehensive U.S. and world coin database; retail pricing estimates; beginner-friendly grading tips. |
| Coins-Value.com | AI-powered identification tool; real-time updates based on recent auction prices. |
| Numista | Extensive catalog of world coins; community-driven ratings; rare coin indexing. |
| United States Mint | Official coin specifications, history, and new releases; perfect for identifying commemorative and circulating coins. |
| Greysheet | Professional-level pricing guide used by collectors and dealers; subscription-based but highly detailed. |
| Smithsonian National Numismatic Collection | In-depth historical context and images for U.S. and world coins, ideal for serious enthusiasts. |
These trusted platforms serve as excellent companions to mobile apps. Together, they ensure that you’re not just estimating the quantity of your coins, but also truly understanding their potential value.
Why Modern Methods Trump Traditional Counting
While weighing and guessing can provide a ballpark figure, using technology adds critical layers of detail:
- Identification of Valuable Coins: Common coins might be worth only face value, but key dates, mint errors, or low-mintage issues could be worth hundreds or even thousands of dollars.
- Accurate Grading Insights: Digital tools often offer basic guidance on the coin’s condition, which is a major factor in determining value.
- Updated Market Values: Online databases and apps pull from auction sales and dealer prices, offering up-to-date figures instead of outdated catalogs.
- Time Savings: What used to take days (especially with large coin jars) now takes under an hour.
In short: Technology turns a simple estimation process into a real opportunity for profit and learning, ensuring no valuable piece slips through the cracks unnoticed.
Tips for Getting the Most Accurate Estimate
- Use a Representative Sample for Large Jars:
If your change jar is overflowing, count and scan a handful of coins first. Use this sample to project the total value. For example, if 100 coins total $12.50, and your jar holds approximately 1,000 coins, you can estimate a rough value of around $125. - Look Out for Key Dates and Mint Marks:
Some coins are rare not because of age, but because of where or when they were minted. Key indicators include:- 1943 copper penny (extremely rare)
- 1969-S doubled die penny (highly valuable)
- 1999 Delaware Spitting Horse quarter (mint error collectors love)
- Scanning coins with an app helps catch these nuances quickly.
- Evaluate Coin Condition:
Coin grading matters. A worn 1916 Mercury dime might be worth $5, but the same coin in near-mint condition could fetch over $1,000. Apps and online resources often give basic grading guidelines:
| Condition | Description | Impact on Value |
| Good (G) | Heavy wear, details visible | Lowest value |
| Fine (F) | Moderate wear, more detail visible | Moderate value |
| Extremely Fine (EF/XF) | Light wear, sharp features | High value |
| Mint State (MS) | No wear, freshly struck appearance | Highest value |
- Cross-Verify with Multiple Resources:
Use both the Coin ID Scanner and databases like Greysheet or Numista to confirm estimates, especially if a coin appears rare or unusual. - Seek Professional Appraisals for High-Value Finds:
If your scan or research suggests a coin is especially valuable (worth $100 or more), it’s smart to get a second opinion from a professional numismatist or certified coin dealer. Some online services even offer free preliminary appraisals.
By blending traditional techniques like weighing and sampling with today’s powerful technology, you ensure that no valuable coin goes unnoticed. Whether you’re planning to cash in your stash, add rare finds to a personal collection, or simply satisfy your curiosity, a thoughtful approach transforms a dusty jar of coins into a mini treasure hunt.
Before you roll up those pennies or feed them to a coin machine, take a few extra minutes to scan, research, and estimate. You might just find that your small change adds up to big rewards.